- Introduction
- Part 1
- Presentation collaterals
- Introduction (p1 & 2)
- Security = PPT (slide 3-4)
- Security across the company (slide 5)
- Management team responsibility (p6)
- Security controls and measures (p7)
- Security is a process, continuously changing (p8)
- How are you doing? (p9)
- How is your customer or supplier doing? (p10)
- Monitoring or Audit: what’s the difference ? (p11)
- Audit types (p12-15)
- Audit main principles (p16)
- Audit red flags
- References
- Feedback
Introduction
This post is the second part on the session on cloud security red flags, I presented on the AICMWC conference in february (AI, Cloud & Modern Workplace Conference 2024).
Down below you’ll find an overview of the various slides with the talking points I covered during the presentation.
Not only attentionpoints, more importantly how to tackle these red flags and security gates to make your Microsoft 365 and Azure environment more secure with low effort security investments by simply implementing a basis cloud security hygiene.
Enjoy and use it to make your cloud more secure!
This post will be updated, going along with more practical security hints and tips, but you can start already.
Part 1
Event material published in this post: Part 1
- Event link: https://aicmwc.azurewebsites.net
- Presentation on Slideshare: https://www.slideshare.net/slideshows/red-flags-and-attention-points-in-cloud-security-audit-watch-the-security-gates/266338983
- Video recording: https://youtu.be/z1gYO5mXM14

Presentation collaterals
Introduction (p1 & 2)
Feel free to connect and link via LinkedIN: https://www.linkedin.com/in/pgeelen/
Overview of my Linked articles : https://www.linkedin.com/in/pgeelen/recent-activity/articles/
Find my Microsoft MVP profile at: https://mvp.microsoft.com/en-us/PublicProfile/5002204

Security = PPT (slide 3-4)
Security is not only built by using technology, you need people to handle the infrastructure and they need instructions and processes to make it work. This combination is called PPT:
- People
- Process
- Technology
Within technology you have both digital as physical infrastructure, that’s why PPT is sometimes referred to as PPPT.
For your information, the new ISO27001v2022 is using exactly these for categories (PPPT).

Security across the company (slide 5)
Security is not only the responsibilitiy of the IT team or cloud security engineer.
Cloud security needs to be tackled throughout the entire company, inluding
- Strategic level
- Tactical level (departments)
- Operational level

Management team responsibility (p6)
Security starts at the top, and should use a PDCA cycle (plan>do>check>act… or Adjust).
(You’ll see that many best practices like NIST and ISO use this approach…)
The management team must provide
- Accountability
- Planning
- Resources
- Operations
- Performance
- Continuous improvement

Security controls and measures (p7)
Withing the security controls and measures, you should (at least) think about…
| Asset management Identity & access management System & network security Secure configuration & baseline Physical security Threat and vulnerability management Application security | Policies & procedures Documentation HR security Supplier Management Incident management Business continuity Disaster recovery |
Whether your talk about your own security, cloud or cyber security… you need these processes one way or another.
Security is a process, continuously changing (p8)
Please be aware that implementing security is not a one-off task, you need to implement security in a continuous way
Typically you can define a lifecycle, with
- onboarding
- change
- offboarding
This is not only applicable to people but also
- hardware
- software
- infrastructure
- assets
- documentation
- processes
- … anything
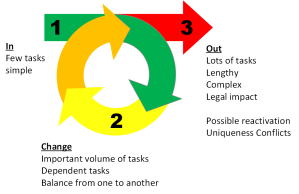
How are you doing? (p9)
In first phase the purpose of monitoring and audit, you target yourself…
How is your company doing
How is your customer or supplier doing? (p10)
Second level, while you can delegate certain activities to external parties, you are still accountable for it..
So you better monitor and audit your externally provided operations closely.
For example, in case of a cyberattack, or a data breach on your supplier, you better investigate the impact to your data and infrastructure…
Info: check the page on Supply Chain security breaches of this blog.
Monitoring or Audit: what’s the difference ? (p11)
| Monitoring | Audit |
| •Performance check •Continuous (or high frequency) •By Owner | •Compliance check •Regular intervals (lower frequency) •Independent from owner |
Audit types (p12-15)
- 1st party (internal audit)
- 2nd party
- Customer > supplier
- Supplier > customer
- 3rd party
- external
Audit types : internal audit
- Self-validation (Auditing within company)
- No publication to external parties
- No certificate
Audit types : 2nd party audit (mutual)
- Commercial interest first
- Contractual dependence
- Due diligence
- Mutual interest
- Customer checking (potential) supplier
- Supplier checking (potential) customer, eg before onboarding
- Delegation / verification of compliance
- Verification if delegated tasks are done correctly
Audit types : 3rd party audit (external)
- Independence between parties
- Auditor vs customer
- No combination of consulting & audit allowed
- Segregation of duties
- Official certificate
- Published
- Available to external parties
Audit main principles (p16)
- Snapshot of situation
- Quick estimation of situation
- Risk based
- Solution based, continuous improvement
Some hands-on experience to stay out of trouble
… detecting the red flags
Audit red flags
1. First login with god mode (p17)
- First login
- First administrator
- has Full power
- “God mode” (super power, can do everything)
Hacker interest
- once captured, full control on entire cloud tenant
Solution
- Create special admin account
- No mail, enable MFA
2. User ID and password
- Typically personal account
- User ID… and just password (an mail address)
Hacker interest
- userid and password of a single account without MFA is easy hack, only need to guess the password
- else use phishing… make you click and login to a false page and gain control over your account
… game over.
Solution
- implement MFA
- by preference use Hardware tokens
- use Passkeys (which is MFA next generation)
3. Default groups
- Azure Groups
- Large volume of Azure and M365 Roles
Solution
- Avoid the use of default groups
- Provide Task based access, granular control
- Only use default groups when no other option left
4. Ad-hoc (eh..no) Identity Management
- Manual management
- No process
- User duplication from existing users
Solution
- Setup basic IDM (identity mgmt)
- Setup IAM (identity and access mgmt)

5. No process management
In many cases the cloud security is set up as a technical platform with
- Manual management
- No process owner
- No process
- No idea how data flows
- No idea on changes
Solution
- Use basic process definitions
- Check ISO9001
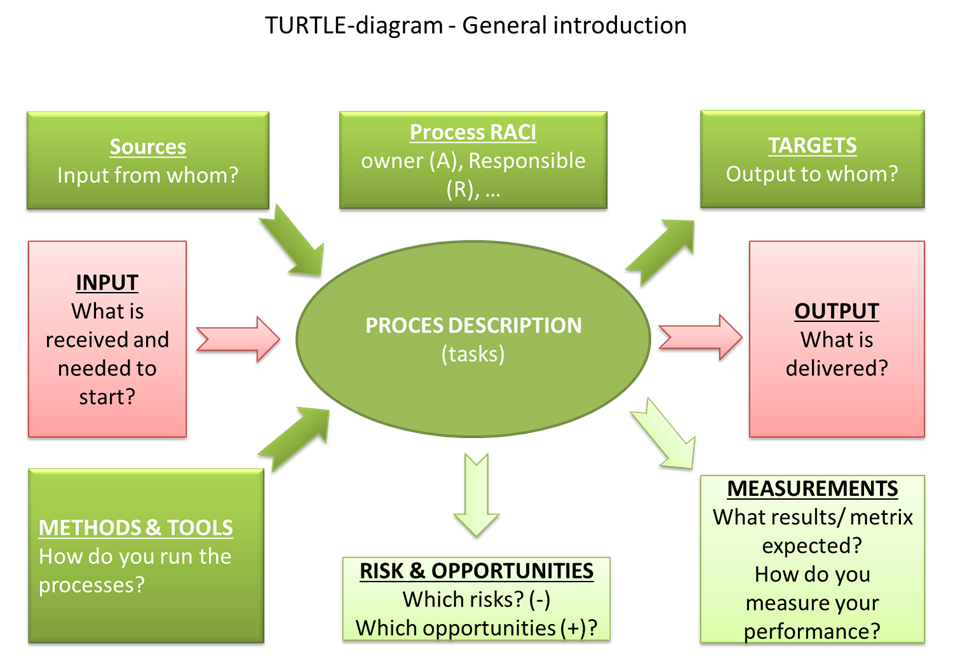
6. All-in one account
In many cases, the account used at first registration is also used for the operational administration later on… which means:
- User account = admin account
- Mail enabled
- Used for office and admin tasks
Solution
- Account separation
- Segregation of duties
- Separate logins for users and administrators
7. All-in one desktop
- •Login account = local admin account
- •Full access
Solution
- Run daily operations as user
- Run admin tasks temporarily as admin
- Provide Admin with specific (task based) access
8. RDP remote access
Typically Azure will suggest to use RDP or Bastion host configuration to adminster your Azure machines …
In a test environment, you might use RDP but by design this is a very security weak protocol, easy to highjack.
- RDP to Azure
- badly protected remote connection
- …
Solution
- use Bastion host
- use other jump host configuration
- login to admin workstation with MFA
- then administer your network from secured admin station)
9. One network
- One network
- Direct connections to Azure
- No segmentation (neither in Azure as physical)
Solution
- Implement network segmentation
- Segment your network on functional level
- Identify normal network flows
- Identify anomalies (abnormal data flows)
- Put Firewalls on every host and every network
10. Onetime configuration
- One configuration fixed at first configuration
- But once set, never reset …
- No review
- No IDM cycle
Solution: check…
- Everytime on new configuration
- During changes
- Check regularly (put it on your agenda
Why not use IDM, the identity management lifecycle.
References
Microsoft
Learn Microsoft Azure audit and logging fundamentals
Azure hardening
ISO standards
- ISO 27001: ISMS (information security management system)
- ISO 27002: ISMS guidance
- ISO 27017: cloud security
- ISO 27018: PII in cloud (data protection in cloud
Cloud security alliance
Cloud security basics (CCSK by CSA)
Feedback
Do you think this post or material needs an update, let me know!
Any suggestion for improvement deserves credits.
The work is never finished, keep improving!
